In a world where cybersecurity threats are growing in complexity, simply securing the server isn’t enough. Mutual TLS (mTLS) is a powerful mechanism that takes TLS/SSL security to the next level by requiring both the client and the server to authenticate each other. Whether you’re building a microservices architecture, an enterprise application, or a financial API, understanding and implementing mTLS can be a game-changer for your security posture.
In this article, we’ll break down everything you need to know about Mutual TLS, including:
- ✅ What mTLS is and how it works
- 🔒 TLS vs mTLS
- 🔧 How to implement mTLS
- 🧰 Real-world use cases
- ⚠️ Common pitfalls
- 📦 Tools and frameworks that support mTLS
What is Mutual TLS (mTLS)?
Mutual TLS is an extension of the standard Transport Layer Security (TLS) protocol that enables both parties in a network connection — the client and the server — to authenticate each other using digital certificates.
Traditional TLS authenticates the server only. mTLS authenticates both client and server.
In simpler terms, imagine a handshake where both people show their IDs before continuing the conversation — that’s mTLS.
TLS vs mTLS: What’s the Difference?
| Feature | TLS (One-Way) | mTLS (Two-Way) |
|---|---|---|
| Server Authentication | ✅ Yes | ✅ Yes |
| Client Authentication | ❌ No | ✅ Yes |
| Use Case Examples | Websites, SaaS dashboards | Microservices, APIs, fintech |
| Trust Flow | Client → Server | Client ⇄ Server |
| Certificate Required by Client | ❌ No | ✅ Yes |
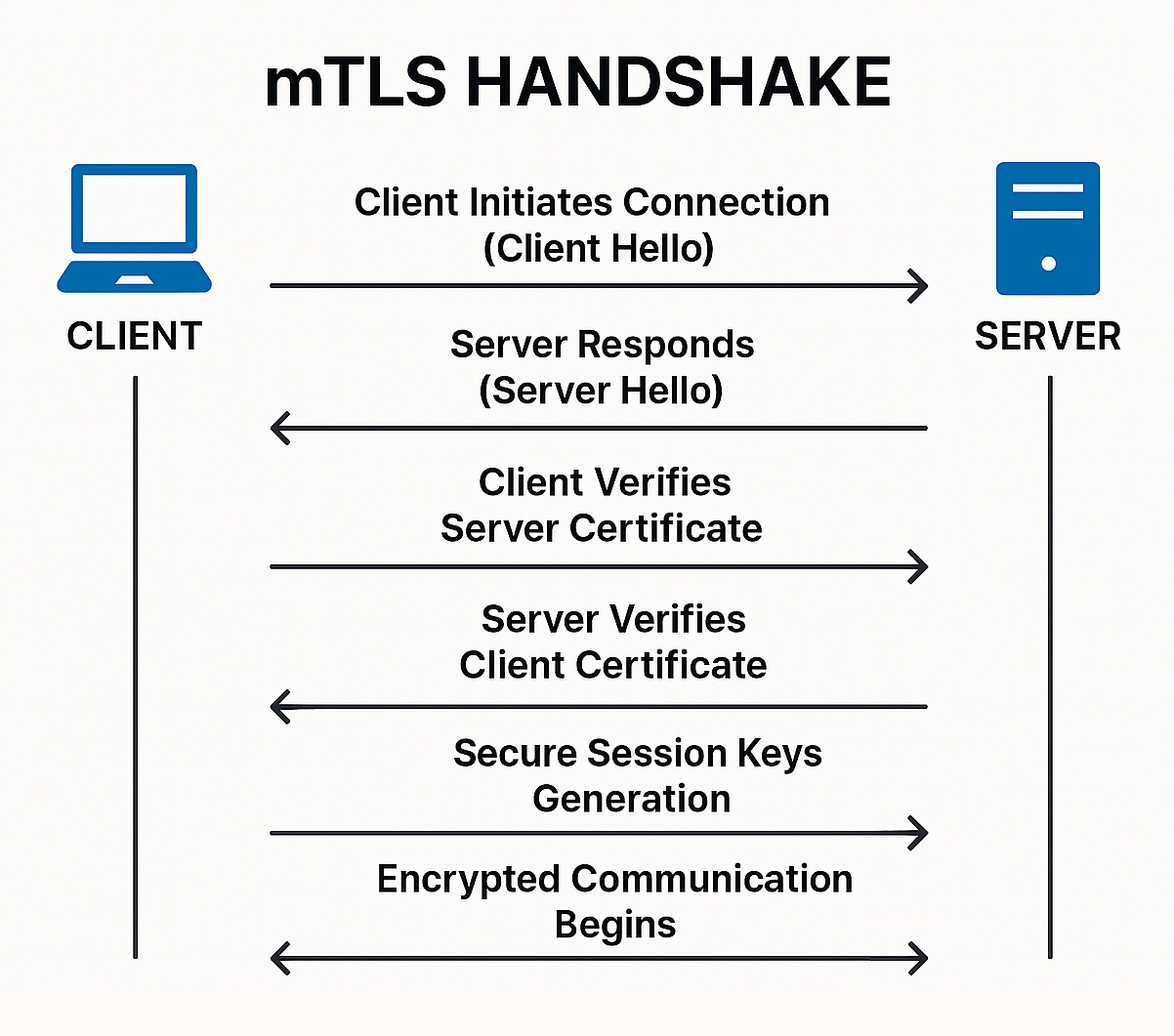
How Does mTLS Work?
Let’s walk through a typical mTLS handshake:
- Client initiates connection to the server via HTTPS.
- Server sends its certificate to the client.
- Client validates the server certificate using its trusted Certificate Authority (CA).
- Client sends its own certificate to the server.
- Server validates the client certificate using its own list of trusted client CAs.
- Once both parties are validated, a secure, encrypted session is established.
Implementing mTLS in Real Projects
server {
listen 443 ssl;
server_name secure.example.com;
ssl_certificate /etc/ssl/certs/server.crt;
ssl_certificate_key /etc/ssl/private/server.key;
ssl_client_certificate /etc/ssl/certs/ca.crt;
ssl_verify_client on;
location / {
proxy_pass http://backend:8080;
}
}Benefits of mTLS
Zero-trust security: Authenticate all parties in the network.
Prevention of impersonation: No unauthorized client can connect without a trusted cert.
Perfect for microservices: Each service can verify its caller.
Compliance: Often required in HIPAA, PCI-DSS, and GDPR-regulated environments.
Common Pitfalls to Avoid
- Improper certificate management
Certificates must be rotated, revoked, and managed securely. - Poor error messages
Without clear logging, failed mTLS handshakes can be hard to debug. - Certificate sprawl
Using automation tools like HashiCorp Vault, cert-manager, or Let’s Encrypt for internal PKI is highly recommended. - Time drift issues
Ensure synchronized time (e.g., via NTP) across clients and servers — expired or not-yet-valid certs can cause handshakes to fail.
Real-World Use Cases
- Banking APIs (e.g., PSD2/OpenBanking)
- Internal service-to-service communication in Kubernetes
- IoT devices communicating with cloud gateways
- Enterprise single sign-on (SSO) systems
- Secure B2B integrations
Tools That Support mTLS
| Tool / Platform | Supports mTLS? |
|---|---|
| Kubernetes Ingress | ✅ (via Nginx, Istio) |
| Envoy Proxy | ✅ Yes |
| Istio Service Mesh | ✅ Full mTLS enforcement |
| HAProxy | ✅ Yes |
| gRPC | ✅ Yes |
| AWS API Gateway | ✅ Yes (Client Certificate Auth) |
| Traefik | ✅ Yes |
Final Thoughts
Mutual TLS provides end-to-end identity verification and encryption. As systems grow in complexity — especially with microservices, zero-trust architectures, and sensitive data — mTLS becomes a must-have.
If you’re serious about hardening your infrastructure, boosting trust, and complying with modern security standards, it’s time to adopt mTLS.
Leave a Reply